What is Mobile Security Threats and Mobile Security Validation?



Mobile Security Threats can compromise the security of mobile devices and applications. These threats can include malware, phishing attacks, data leakage, unauthorized access, insecure data storage, and unsecured Wi-Fi networks. To address these threats, mobile security validation is crucial.



Mobile Security Validation involves assessing the security controls of mobile devices and applications, identifying vulnerabilities and threats, and ensuring that security best practices have been implemented. This process can include penetration testing, static and dynamic application security testing, code review, compliance auditing, and threat modeling.
What is Mobile App Security Validation?
Mobile application security validation is the process of identifying potential security vulnerabilities that may put users’ data and privacy at risk. For instance, analyzing the code, design, and functionality of the mobile application to determine potential security flaws and weaknesses that can be exploited by hackers or malicious actors through automated or manual processes. Additionally, insecure data storage, improper authentication and authorization, insecure network communication, and other issues that may arise due to flaws in the application’s design or implementation.
The main goal of mobile application security validation is to ensure that mobile applications are designed and developed with security in mind, and that they met industry security standards to protect sensitive user information. Ultimately, this translates into a safe user experience. It is essential that the mobile application development process is conducted regularly to stay ahead of emerging threats and vulnerabilities.
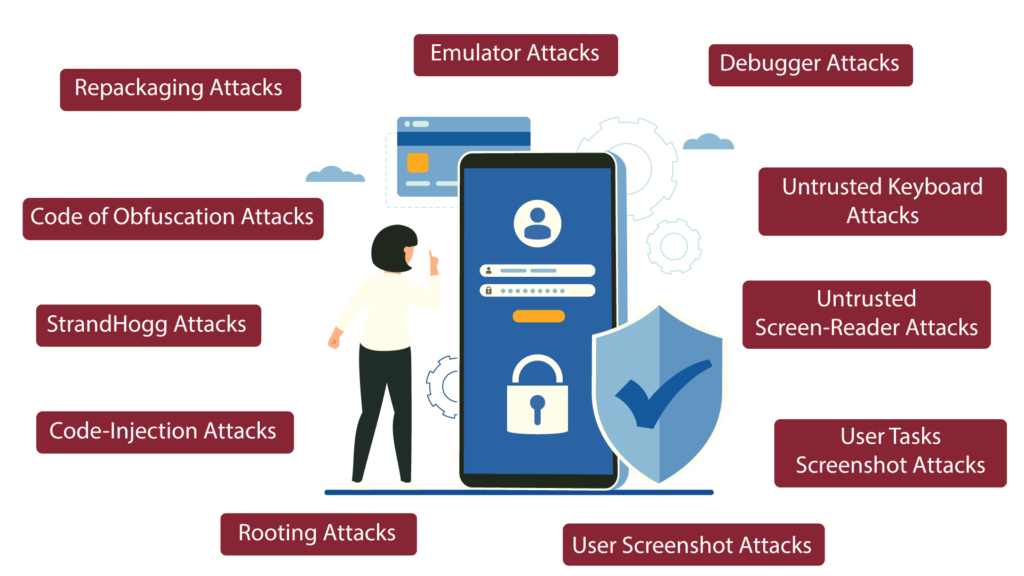


What are the types of Mobile App Security Validations?
The primary objective of mobile app security validation is to identify vulnerabilities, with the secondary objective of implementing security best practices and meeting specific security standards.
Possible harmful attacks on mobile apps are identified below:
- Repackaging Attacks
- Simulated Repackaging attacks is conducted through modifying legitimate mobile apps by inserting malicious code, the app is vulnerable in a way that the users will be exposed to security risks.
- Emulator & Debugger Attacks
- Emulator and debugger attacks are techniques that exploit mobile devices and applications. Emulator attacks simulate mobile device behavior and inject malware to steal information, while debugger attacks manipulate an app’s security mechanisms to access sensitive data or control its behavior. Both methods can be used to bypass security controls and are employed by attackers to exploit vulnerabilities in mobile devices and apps.
- Untrusted Keyboard and Screen-Reader Attacks
- Untrusted keyboard and screen-reader attacks are simulated to involve malicious apps that intercept and steal sensitive information. The former attack involves intercepting keystrokes, while the latter intercepts and transmits sensitive information displayed on a device’s screen. Both attacks are designed to exploit vulnerabilities and steal sensitive data.
- User Screenshot & Tasks Screenshot Attacks
- User and task screenshot attacks involve taking screenshots of a mobile device to capture sensitive information. User screenshots are taken to steal information from the device, while task screenshots are taken during specific activities such as password entry. Both attacks aim to exploit vulnerabilities and steal sensitive data from the device
- Rooting Attacks
- Rooting will be simulated by means of gaining administrative access to a mobile device’s operating system as such attacks’ aim is to gain access to the device through bypassing of the security mechanisms to gain access to sensitive data
- Code-Injection Attacks
- Code injection attacks are simulated by means of injecting a malicious code into an app’s memory to manipulate its behavior thus potentially accessing sensitive information or performing unauthorized actions.
- StrandHogg Attacks
- StrandHogg is a type of Android malware that disguises itself as a legitimate app and allows attackers to hijack apps and steal sensitive information, such as login credentials and banking information. Thus, StrandHogg attacks will be simulated to see if such malware can evade detection and display fake login screens to capture user information
- Code of obfuscation Attacks
- Code obfuscation attacks is simulated to check for is a technique in mobile security that makes it harder for attackers to understand the code of an app. Code obfuscation attacks involve malicious attempts to bypass these techniques.
Introducing YESSAFE AppProtect+, the app security shield which protect end-users from sophisticated malware attacks on mobile apps. It also provides vulnerability detection, app protection via Runtime Application Self-Protection technology, and App Usage Information to respond to the real threat of sophisticated malware.
AppProtect+ is EMVCo certified and recognized by Gartner, a leading global technology research and consulting firm.
Speak to our specialist today to find out how you can validate your apps or to understand how you can protect your apps through our solution YESsafe AppProtect+.

