


A recent news dated on 10th Mar 2023 from The Straits Times titled, The Big Story – Military Docs Leaked Online, where leaked confidential defence documents have been put up for sale online by hackers. The report states that at least 2 Singapore entities were listed in the leaked documents. Even though the leaked military documents do not contain current or any sensitive documents and is still under investigation. This news certainly brings us into thinking what can be done to secure these documents. Are there any Document Security solutions available?
What is Document Security?
For any organisation, effective communications have to be made across all channels (from customers, employees to stakeholders) and most of the time it carries valuable and important information (which at times are classified or even confidential in nature). Due to this fact, we should be concerned on the very fact of how secure is this document? Is it safe from ill-intent parties?
Well, on this basis, document security, sometimes known as document access security, are dedicated security procedures that are put in place to deter data manipulation and reproduction of critical or strategically important documents that can be shared safely internally and externally.
What are the common practices?
The usual practices that were adopted, including password protection, provide only secured document sharing links to intended parties. But is this enough? Are we able to secure our document in this way?
Therefore, to determine if our documents are actually secure, let us take a look at the life cycle of a few documents security requirement to see if our documents are in a secured state at this point of time.
The life cycle of a document revolves around 3-stages: processing, transit and storage. Documents will be at risk if access approvals and audits are not in place. Though we can send documents to the intended party, but documents can be hijacked while in transit. In storage, we can always set password implementation on the user access but unfortunately most of the time hackers can easily “pass through” this protection and when they do, they have full access to all of our documents.
When we understand the lifecycle of a file, we can then observe what can be done to greatly improve the data security of our documents.
ABAC (Attribute Based Access Control)
Digital transformation has greatly created new ways to work smarter and faster regardless of location and time. Also, with the increased needs of collaborating on and sharing sensitive or classified information, new security risks and problems have evolved and need to be resolved.
One of the possible threat vectors could possibly be – insiders. According to a report by Ponemon Institute published in 2020, globally the cost of insider threat which involves negligent employee or contractor accounts for up to 62% of security incidents with malicious insiders contributing another 23%. Hence, data security that addresses insider or external threats is paramount for enterprises, government, defence industry, research, intelligence as well as supply chain collaboration.
Traditional security tools are focused on protecting systems from external threats. To address insider threats a new security model is needed that focuses on directly protecting what is at stake – DATA.
Hence, Attribute Based Access Control (ABAC) is the solution.
Why ABAC?
Attribute Based Access Control (ABAC) is a Zero-Trust, data-centric security model that uses dynamic policies to control who accesses information and under what conditions.
With an ABAC-enabled solution, policies can be based on any combination of user attributes, content and environment attributes. This methodology allows the governance and security teams to create policies that dynamically adjust access, usage and sharing rights based on real-time comparison of user context and file content to enforce regulations and policies.
ABAC policies will ensure only the right people can access the right information at the right time.
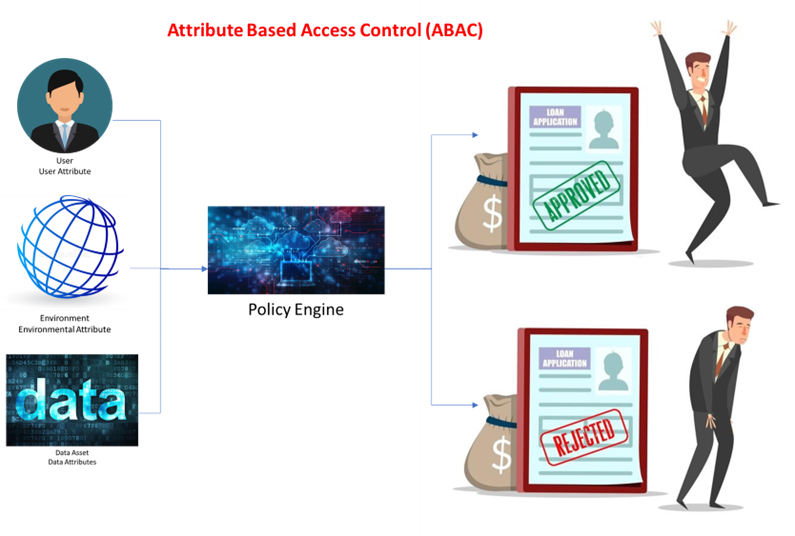


How does it work?
The ABAC model uses attributes like document, user and environment values. A dictionary of attributes is created to build precise access control and data protection policies. A policy is then setup to determine the access rights to the document. By using the combination of the various attributes, we can set forth the access policy to the document and hence enhancing the security of the documents.
Application of ABAC
In summary, a good document security should adopt the ABAC policy to determine the access rights to the document. With ABAC methodology in mind, I-Sprint partnered with archTIS, a global provider of innovative software solutions for the secure collaboration of sensitive information and its award-winning data-centric information security solutions to protect the world’s most sensitive content in government, defence, supply chain, enterprises and regulated industries through attribute-based access and control (ABAC) policies.
Our Secured Document Solution includes the following functionalities:
- Discover and Classify – Our Secure Document solution scans and inspects files in on-premises and cloud collaboration apps for sensitive or regulated data according to defined policies. When detected, it automatically classifies the file and applies information protection based on Its sensitivity and your policies. It can also leverage MIP sensitivity labels in combination with other file and user attributes to control access to and apply information protection.
- Restrictions – Utilise granular security to automatically restrict access to, sharing of and protection of content based on the business rules associated with the file’s classification or MIP sensitivity label. Access to a file can be restricted to a specific individual or group, even if a wider audience has access to the rest of the site where the item physically resides. Managing access at the file level is made possible by leveraging the data and user attributes, rather than the data location.
- Encryption – Our Secure Document solution can further secure content by encrypting it to ensure only properly authorised and credentialed users will be able to access the content even If they have administrative privileges, making It safe to store confidential documents such as Board or HR documents. It also ensures access can be controlled for any data shared with external parties, even when it is removed from a site.
- Prevention – You can also define rules in our Secure Document solution to prevent the distribution of sensitive information or confidential documents to minimize the risk of data loss. For example, if a file Is added to a site and member does not have proper access to that category of document, then the file can be hidden from the view of the unauthorized individual. Users can also be prevented from printing, emailing via Exchange, saving or copying the contents of Microsoft Office documents and PDFs outside of the Office 365, SharePoint or OneDrive.
- Access Control – sing workflows, our Secure Document solution can trigger access approval requests for policy officers or managers or to request Justifications from users. Complete business rules can be developed so that you can remediate compliance issues and task the proper individual(s) in the organization to review and potentially classify, alter the classification of, or encrypt the content.
- Unique Data Protection Capabilities – Our Secure Document solution works natively with Microsoft collaboration and security products to augment native features to enforce secure read-only access, hide sensitive files from unauthorised users, trim the application ribbon, apply dynamic personalised watermarks, and encrypt or restrict attachments sent through Exchange Email.
- Redaction – Our Secure Document solution can remove/redact sensitive or confidential information, such as keywords or phrases, in a document when viewed In Its native application (Word, Excel, PowerPoint and PDF) or when the file is presented in the NC Protect secure reader for legal or security purposes.
- Audit & Report – A dynamic Results Viewer provides centralised reporting and management of classified data. Report on the number of issues identified by classification level and allows policy officers to review the results and rescan, reclassify or reapply permissions if needed. Integrate user activity and protection logs with SIEM tools like Splunk or Microsoft Sentinel for further analysis and downstream actions.
These functionalities are getting wider recognition in important and strategic areas such as Government, Defence, Financial Services, Critical Infrastructure, Healthcare and Legal.
Talk to a specialist today to learn more.

