i-Sprint Uncovers Sneaky Android Banking Malware, FjordPhantom
New Malware Threat Detected

Promon and i-Sprint recently uncovered a new Android malware spreading across Southeast Asia. Out of the 113 banking apps tested, an alarming 80.5% cannot protect against FjordPhantom.
How Does It Work?
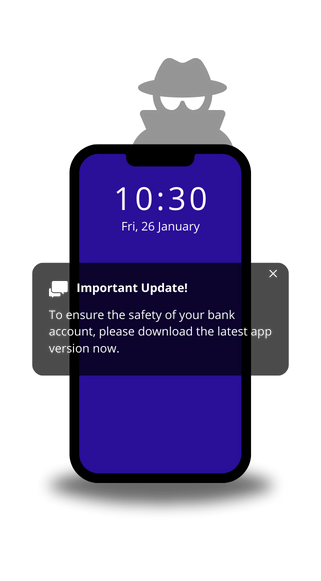





Distribution
- FjordPhantom targets banking customers with deceptive app downloads, using sophisticated social engineering tactics.
- Primarily spreads through email, SMS, and messaging apps
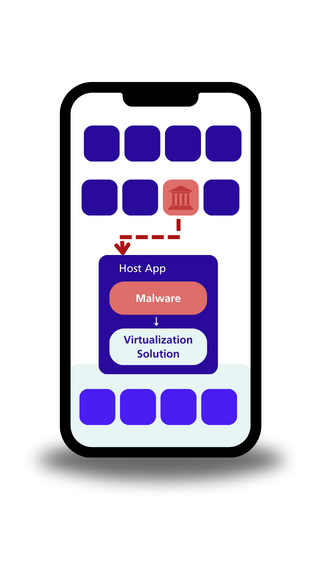





Virtualization
- FjordPhantom employs an unprecedented virtualization technique, eluding user detection and security measures.
- This allows the malware to utilize its hooking framework, enabling multiple apps to operate within the same sandbox
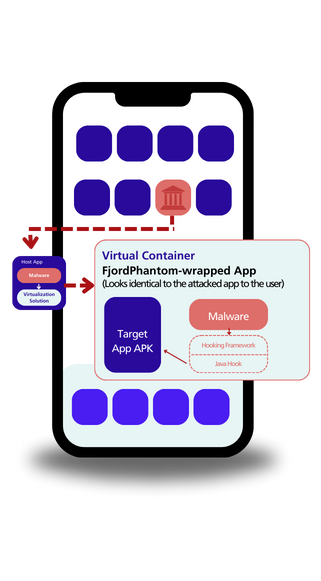





Hooking
- Code Injection: FjordPhantom injects malicious code into banking apps, manipulating Accessibility and GooglePlayServices APIs for detection evasion.
- UI Manipulation: The malware hooks into UI functionality, automatically closing dialog boxes to avoid raising suspicion.
- Stealthy Logging: FjordPhantom strategically places hooks to log target app actions without altering their visible behavior.






Attack
- Orchestrates a comprehensive attack for stealing sensitive information and manipulating user interactions within the app.
- Exploits the virtualized environment to execute real-world fraud, evading conventional security measures
The good news? We’re ahead of the curve.
Our latest release of AppProtect+ includes a powerful solution to detect and neutralize FjordPhantom.
Find Out If Your Company App Holds Up Against Fjordphantom:
i-Sprint Uncovers Sneaky Android Banking Malware, FjordPhantom
Promon and i-Sprint recently uncovered a new Android malware spreading across Southeast Asia. Out of the 113 banking apps tested, an alarming 80.5% cannot protect against FjordPhantom.
Challenges in securing Structured vs Unstructed Data
According to IPH, it detected unauthorized access to its document management system which stored its own administrative documents as well as that its clients and their correspondences......