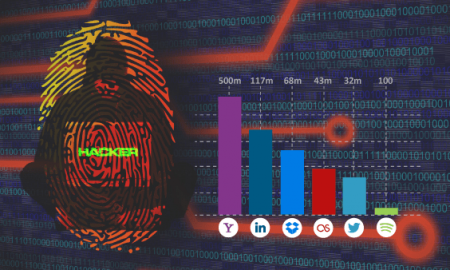
500 million from Yahoo, 117 million from LinkedIn, 68 million from Dropbox, 43 million from Last.fm, 32 million from Twitter, hundreds from Spotify, these are not the new sign up numbers, but the number of accounts that have been hacked! It may seem on the surface as a users’ account credential leak issue, but the underneath implication is far greater as most users use the same password across different services/ applications.
Hackers break into a company’s internal network and attempt to get a copy of the password database. The cost and time required for password brute force attacks have significantly gone down. The cracked password data is then sold on underground darknet markets to break into the user’s other accounts or used to hold the company ransom. The leakage of such data can lead to penalties from regulators, affect the corporate net worth and more importantly cause customers to lose trust in the companies offerings.
To prevent exposure of sensitive data, enterprises need a strong data protection solution such as end-to-end encryption (E2EE) to protect passwords and sensitive transaction data. E2EE ensures that sensitive data stays encrypted even within the memory of vulnerable web or application servers. It prevents insiders such as software developers or database administrators (DBAs) from leaking sensitive data accidentally or deliberately.
i-Sprint Universal Authentication Server (UAS) E2EE for Credential and Transaction Data Protection solution has been designed to meet the E2EE requirements. It is a complete end-to-end encryption solution that is bundled with a FIPS certified Hardware Security Module (HSM) and user endpoint encryption libraries that support all major web browsers as well as Apple iOS, Android, Blackberry, Windows mobile platforms.
i-Sprint UAS E2EE solution is a proven solution among many financial institutions and provides an off-the-shelf product to enable organizations to encrypt the password and sensitive data and send the encrypted data over a communication channel in addition to the SSL protection. This is done by using an encryption library and key data to encrypt the data at the point of entry (user desktop/smartphone) before submission to the server side. This data remains encrypted all the way to the web server and even the application server. The data may be decrypted at the application server, however, in the case of passwords, they remain encrypted and are verified inside a HSM. HSMs are cryptographic devices using tamper resistant hardware built to meet the FIPS standards. Thus the passwords are encrypted from the point of entry to the point of comparison. This also ensures that nobody in the intranet has access to the password in clear during transit and storage, as well as protecting against internal fraud.
In summary, effective data protection requires a combination of layered security solutions and the right processes. Organizations should not wait for the next web server vulnerability or the next attack and should look into implementing End to End Encryption solutions at the application layer to protect their confidential information.
